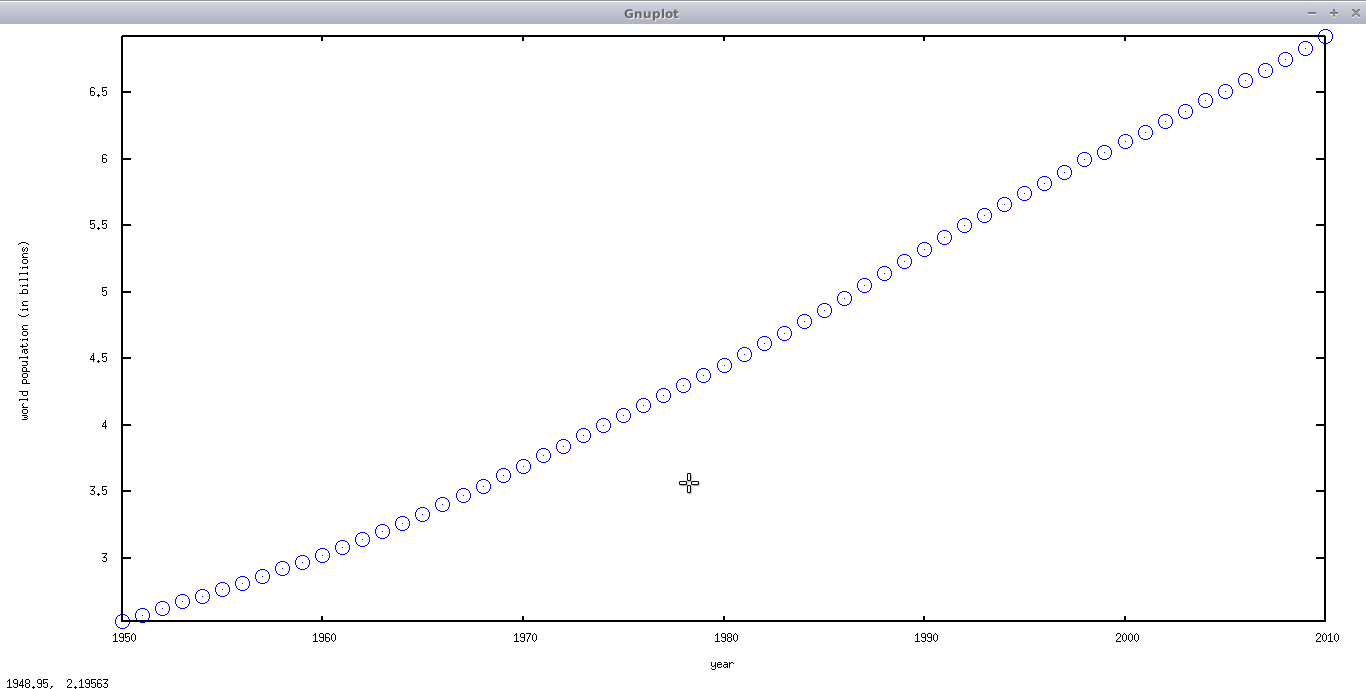
I’m sure everyone has heard of “culture” but the American educational system never really gave me a good idea of what “culture” is. So let me try to explain it.
I currently live in Missouri; however I moved here from Ohio.
When I first moved here I noticed that everyone referred to Carbonated beverages
as “soda”. I however had always referred to it as “pop” as did all of my
friend in Ohio.
I had also noticed many other differences in the way
people acted here. There were many little details that were different.
They drove in a way that was far less safe. They had read different children’s books as kids, they had an obsession with hot sauce, etc.
I later found out that all these little differences are
differences in “culture”. People from one isolated region in the world
act very differently from people in another isolated region.
I can not tell you how many arguments I had
gotten into with people about the proper name for these carbonated drinks.
It wasn’t until recently that I realized that this is why humanity is on a
path to destruction. Not because we call carbonated drinks by the wrong name, but
because of how we treat people of different cultures.
There is something deep within the human mind that causes us
to become angry with people who are too different from us. When I
came to Missouri people were angry enough to get into arguments with me
over the proper name for fizzy drinks. These arguments I had gotten into are
perhaps some of the stupidest ones I’ve ever had because they are arguments
about the least important details in the world.
Now think about this on a global scale. Cultures can have much bigger
differences between them. Some cultures can be so different that someone
from one culture literally can’t communicate with someone from another culture
because they speak two different languages (and yes language is in fact a part
of culture).
Some of these differences can lead to wars between different countries.
We often can get so angry at someone for being different that we can
feel the need to kill them.
Do not worry though; for I, like a good con artist salesman, have a solution for the problem (or at least part of one), and that
solution is understanding.
To anyone considering becoming a soldier so as to bring world peace, please don’t. War can not bring peace. As JF Sargent from Cracked.com said
“If you’re trying to violence somebody into being peaceful then you don’t understand violence, peace, or words in general.” -JF Sargent
What we need is not war. What we need is understanding.
Understanding is what has led us to countless amazing accomplishments.
We have created thinking machines (aka “computers”) and have sent them across the infinite void of nothingness to other worlds altogether
so that they could allow us to see what they have seen by using invisible beams of light. We have built a vast network of these thinking
machines so that we can instantly share our thoughts, ideas, stories, knowledge, and wisdom with people around the world. We have
taken to the skies using machines that we built using our understanding of the world. We have reached out across the infinite void and touched our
own moon. We have created shelters for ourselves that can protect us from dangerous elements.
We have done all these great things and countless others because we gained an understanding. For those things we used SCIENCE which
is a process we can use to gain understanding.
“Science is the best tool ever devised for understanding how the world works.” (Michael Shermer).
With science we have understood how nature works by simply following the process. We came up with psychology, and neurology to understand our own minds,
mathematics to master the art of logic, chemistry to understand the materials around us, biology to understand our own bodies and the bodies of all other
living things, and physics to understand the physical world (as you can tell by the name, physics is the most all-encompassing science because it
is the original science and the most sciencey science).
World peace will be all too easy to accomplish once we have an understanding of different cultures.
Misunderstandings have led to many great wars, but a bit of curiosity from everyone, and some healthy skepticism can do wonders to fix that.